Consider this an update to a previous article where I talk about using rebel.ca to manage my DNS records. I still like them as a company, and the support is generally good – I will no longer recommend them. Without getting into the details, I had a DNS management problem with them that was the last straw for me, this resulted in about 36hrs of downtime for this domain.
The good news is that today, there are lots of free managed DNS providers. Really this isn’t a huge technical challenge. You need two nameserver entries in your SOA that is managed by your registrar. Ideally those nameservers are hosted on machines that are on different networks and in different locations for good redundancy. As far as management of the record, having a friendly web UI isn’t a huge problem in 2024. These servers will answer DNS requests for the many DNS servers out there that ask for a name to IP mapping. Yes, there are real costs to operating one of these – but for an individual personal domain, the number of queries and amount of data is pretty tiny.
I decided to go for Cloudflare, they offer a generous free plan and are pretty central to the operation of the internet as a whole. Hopefully I can trust them to manage my DNS record(s), but I do have some reluctance because the internet is dominated by a few huge tech companies which isn’t great. I believe the internet needs to be built on open standards and we need lots of medium sized companies providing services.
You can sign up for Cloudflare in minutes. Entirely self service, and email confirmation is used to give you full access.
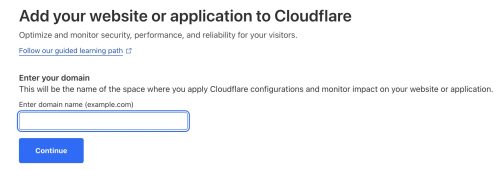
Adding one of my domains to be managed by Cloudflare is easy. I want to click on the ‘Website’ entry on the left navigation bar. Then I pick +Add a site to enter the domain I want them to manage DNS for.
Now we pick the ‘Free’ plan and move to the next step.
Cloudflare does a pretty slick job of sniffing out your existing DNS records (assuming you have some) and populating it’s configuration. Review these and edit as needed. Then we can continue.
As I mentioned above, I really don’t want Cloudflare messing with things much – so I disabled the “Proxy” for all of my records and have it setup as DNS only. If I ever have a problem, I can go in and use some of their free DDoS protection stuff – but let’s start with just the basics.
To enable Cloudflare to be my DNS provider, I need to go change the record with my domain registrar so that it points at the Cloudflare name servers. Cloudflare monitors this and will make my domain ‘active’ in the dashboard, but they’ve already created the DNS records and things are good to go. It was a matter of minutes for my domain to become active once I’d modified the SOA with my registrar.
I did this back a few weeks ago. So far so good, but then again DNS is pretty boring when it’s not breaking the internet.