 Wow – where did the month of June go? I’ve kept busy, but haven’t been very good about posting to the blog – I’ll try to get back to my once a week posts.
Wow – where did the month of June go? I’ve kept busy, but haven’t been very good about posting to the blog – I’ll try to get back to my once a week posts.
Recently my Dad rediscovered my blog and found the iPhone 3G with 3.1.2 post. He also has an older Rogers iPhone 3G and wanted some help unlocking it for use with any carrier, especially for use in the States.
He had upgraded the iPhone 3G to 4.2.1. This came along with the baseband (modem) version 05.15.04. I believe that 4.2.1 is the most current version of iOS that can be run on this generation of the hardware, and from what I’ve been told many feel that 3.1.3 is better performing but will prevent you from running some of the more recent applications that require newer features.
One of the problems with 4.2.1 is that while it can be jailbroken, it doesn’t have an unlock due to the baseband (modem) version. So my first thought was – why not just put the phone into DFU mode, and install 3.1.3 on it?
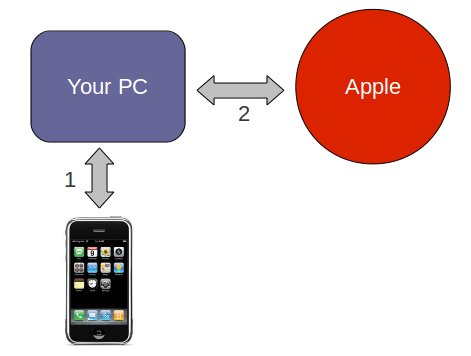 This is where I ran into the first problem. The firmware installed just fine, but we then got a 1015 error. There are two steps that happen when you’re installing a new firmware on your iPhone. (1) The firmware is installed (2) your PC calls home to Apple to verify the firmware. There is a good write-up on this by Jay Freeman (saurik) that goes into details (read up on the signature server).
This is where I ran into the first problem. The firmware installed just fine, but we then got a 1015 error. There are two steps that happen when you’re installing a new firmware on your iPhone. (1) The firmware is installed (2) your PC calls home to Apple to verify the firmware. There is a good write-up on this by Jay Freeman (saurik) that goes into details (read up on the signature server).
At this point I allowed iTunes to just restore back to 4.2.1 to get the phone back into a working state. Still not deterred, I figured there had to be a way to solve this problem. There is probably more than one solution, but I’ll focus on the one I used: it turns out that you can downgrade your baseband (modem) in 4.2.1 IF you have the right bootloader (5.08).
I used tiny-umbrella to check the bootloader vers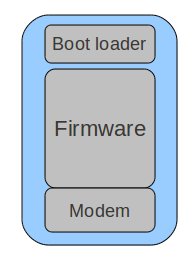 ion, I puzzled a bit over the information it was providing until I realized the bootloader version was tacked onto the end of the modem version. This is actually not a required step as the downgrade process will check for the correct bootloader anyways.
ion, I puzzled a bit over the information it was providing until I realized the bootloader version was tacked onto the end of the modem version. This is actually not a required step as the downgrade process will check for the correct bootloader anyways.
On the right is my conceptual model (potentially incorrect) of how the iPhone lays things out. There is the bootloader which is a little bit of code that runs when the phone is powered on. It knows enough to help recover if things are in a very bad state and there appears to be no firmware – or we’re in DFU mode. Breaking the bootloader would be a very bad thing.
The firmware and modem (or baseband) are bundled together for distribution, but occupy unique areas in memory and are installed somewhat independently. There are a number of hacks which allow you to prevent the modem from being upgraded (allowing for unlocking to still work).
My understanding of iPhone unlocking is that most of the unlocks are software tweaks to the modem. This is not a true unlock, but a patch that is run each time the phone is booted (or possibly more often). The reason you need to jailbreak your device in order to unlock, is you need to run some unsigned code to unlock the phone. No jailbreak, no unlock.
So, assuming you’ve got the 5.08 bootloader the steps are:
- Jailbreak 4.2.1 with redsnow (the latest)
- Launch Cydia and install FuzzyBand
- Modify FuzzyBand with a new ‘cert’ (download ICE2-05.15.04.cert)
- Run FuzzyBand to downgrade the modem/baseband
- Install ultrasn0w via Cydia
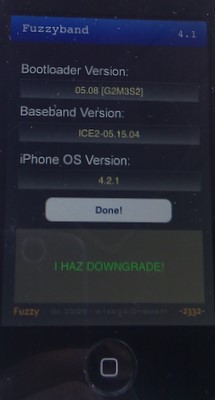
That’s it. At the end of step 4 you’ll see the “I HAZ DOWNGRADE!” as pictured at the top of this post.
I find it a bit odd that FuzzyBand in Cydia needs to be modified with an additional ‘cert’ file to identify the 05.15.04 modem/baseband. I used a trial version of DiskAid as I was using a Mac. The modification is simply reaching into the FuzzyBand application installed on your iPhone using DiskAid and adding the cert file to it, very easy. If you don’t modify FuzzyBand, it will refuse to downgrade the 05.14.04 modem, it also appears to check that you’ve got the right bootloader (I did) – so it tries fairly hard to be helpful.
Now that your phone is jailbroken and unlocked, sync it to iTunes to recover all of your apps an files. Do not upgrade the firmware again – or you will be back to square one (or worse, possibly locked out). Also consider capturing your SHSH blob.


