I’ve been on DSL forever. I started out on Bell, have been on NCF, and most recently TekSavvy. I’ve had my trials and tribulations with DSL, and have a collection of DSL modems (some are backup, some are bad, some were sensitive to line conditions).
Cable has always been a faster alternative, but it meant I needed to pay a cable install fee and switch technology in general. Also, a static IP wasn’t possible on cable – and having self hosted lowtek.ca for a long time, I’ve always felt a bit trapped to DSL to give me a static IP.
DSL can be fast, but not in my area which seems to have been left behind for faster connectivity. The highest speed I could get was 15 down, 1 up. Now, 15 down is great – I can stream HD Netflix without any real problems. The internet feels fast enough.
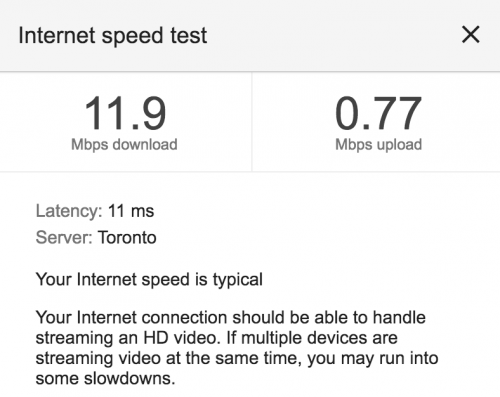
I have to say, I really appreciate that Google has built a good enough speed test that is easy to use.
One motivating factor was my desire to stop paying Bell for my land line. It’s nearly $50 a month and we barely use it. Sure I could switch to a VOIP provider but then I still have to pay for the dryloop cost and it sounded like I’d probably experience a service outage (of up to 5 days) when the line switched.
Moving to cable means losing the static IP. It also means that outgoing port 25 is going to be blocked and this means my self hosted email server will have problems.
I’ve sketched out a solution for static IP hosting. I’ll try to write that up in the future once I’ve done it. For now, because on cable your IP rarely changes – I’m just pretending that the IP I have is a static IP.
For sending email, I needed to route all my mail via Teksavvy, treating them as a smarthost. My email setup is postfix, thus there is literally a one line setup change to /etc/postfix/main.cf
|
|
relayhost = smtp.teksavvy.com:25 |
This works because TekSavvy allows anonymous SMTP to this from inside of the network they control. What it does is force all outgoing email to be sent to their server, which in turn will send it out.
Now modern email servers do additional trust checks, one of these is Sender Policy Framework (SPF). Configuring your SPF is done via a TXT record in your DNS. While the relayhost was working, I was seeing a warning when checking email sent to gmail (but other email providers check SPF too).
|
|
Received-SPF: softfail (google.com: domain of transitioning testmail@lowtek.ca does not designate 76.10.157.38 as permitted sender) client-ip=76.10.157.38; Authentication-Results: mx.google.com; spf=softfail (google.com: domain of transitioning testmail@lowtek.ca does not designate 76.10.157.38 as permitted sender) smtp.mailfrom=testmail@lowtek.ca |
It took a while for me to figure out how to get my SPF record setup correctly. I got a bit lucky, as I was reading https://support.google.com/a/answer/33786?hl=en which pointed at _spf.google.com as the Google SPF record holder. It turns out TekSavvy adopted the same naming: _spf.teksavvy.com. Your SPF record needs to point at other SPF records, so finding this meant it was an easy change to my DNS TXT record for SPF.
|
|
v=spf1 a mx include:_spf.teksavvy.com ~all |
I will point at MXToolBox as a great web based tool for sorting out all sorts of email issues.
Now email was not only working via the smarthost, but my SPF record was setup correctly. I’m still experiencing delays when sending to gmail, but not apparently to other sites. From looking at the headers, it seems TekSavvy can at times (often) delay delivery to gmail. This is frustrating, but there are other paths to solution if it’s a big problem.
Now that email was sorted out, switching to cable was really easy. The cable box arrived and was “installed” by finding the live cable in my basement by the power panel and plugging the box in. It turns out that since the cable comes from a box at the end of my lawn and the buried cable to my house (which is 20yrs or more old) is in good shape, I get fantastic signal strength. The tech had to install an attenuator to reduce the signal to the happy range where the modem was going to work well.
Switching from DSL with static IP to Cable with rarely changing IP was a simple matter of swapping the WAN cable into my router from one box to the other. I had to reconfigure my router to use “Automatic” from “PPPoE”, and boom I was on the internet again. Visiting https://www.whatismyip.com/ and I had the new IP address, followed by a simple DNS change to use that as the address for lowtek.ca and I’m back.
At this point all I’ve lost is the reverse DNS check is failing, because the IP that lowtek.ca resolves to – does not answer lowtek.ca when you look up that IP. This is more important for sending email than receiving, and since I’m sending via Teksavvy it doesn’t matter as much. I still want a more ‘proper’ static IP to be assigned to lowtek.ca – more on that in a future post.
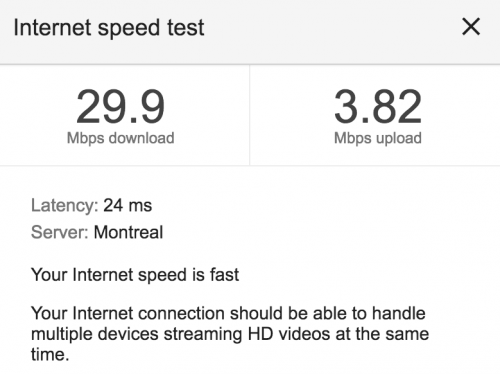
Boom – cable is just faster than DSL. With the added bonus that changing speeds is zero admin costs. If I want to move to 2x faster, it’s another $7 a month. On DSL I was at the fastest speed available to me at my location. Cable is costing me about $14 more a month, but the phone line savings will make up for that – once I get past the hump of buying a new cable modem and VOIP ATA box.


